If you have heard of the buzzing word, Red Teaming over and over again and want take a dive into the world that is beyond regular Pentesting which mostly relies on exploiting the known vulnerabilities, then CRTP can give you the perfect start.
Certified Red Team Professional (CRTP) is the beginner level course + exam from Pentester Academy that introduces you to the world of Active Directory Security. It does not focuses on exploiting the patchable vulnerability but rather the misconfiguration which is very common even in the organization which has higher security maturity level.
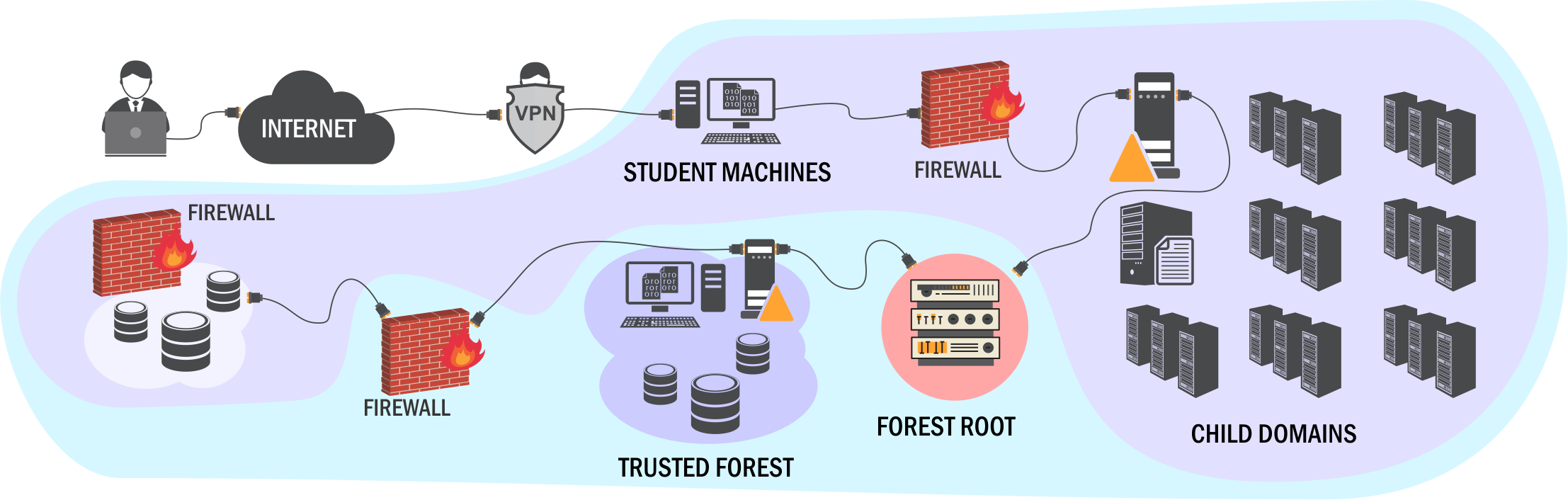
One thing to mention here is that the course uses Windows based environment to exploit the attacks using PowerShell based Tools which might be slightly different If you are planning to conduct the same from Linux based machines. However, the concepts remains same and it is a matter of switching tools and using another set of tools from your arsenal.Is this course for me?
- If you are fresher in the world of security or a seasoned offensive pentester, for sure you are going to learn a lot and develop new attack tactics which are beyond Nessus + Metasploit. It is also good to cover the AD Security concepts for the people who are planning to take OSCP.
- If you a defensive security professional, you also can learn what the bad guys think and how they plan their attacks. What footprint do these attacks leave on the machine and the network which can be used to create rule and monitor such behaviour in the SOC environment
I will divide my review in 3 parts as:
1) Preparation
If you are one of those who likes to sharpen the sword before entering the arena, then it is recommended to do some home work to save lab time. Especially if you are new to the concept of Active Directory. Below are some recommendations:
- Concepts
- Domain Enumeration: Users, Group, Computers, OU & GPOs, ACLs and Domain Trust
- Gaining Initial Foothold: Kerberosting, ASEPRoasting, Stored Secrets etc
- Delegation based attacks: Constrained & Unconstrained
- Privilege Escalation: Local PrivEsc
- Lateral Movement: Find the local admin access & Search for logged on session
- Persistence: Golden Ticket, Silver Ticket, Skeleton keys & Inter-Realm Golden tickets
- MSSQL - Exploitation and Lateral movement
- Tools:
- Powerview
- adPEAS
- PowerUp / beRoot
- Mimikatz & Rubeus
- BloodHound & Sharphound
- PowerUpSQL
- Home Lab Setup
2) The Lab
- How much lab time should I buy?
After your purchase, you will get instant access to Student Portal having Course Video + Course Slide (PDF) + Lab Manual + Tools Set.
- The lab time does not automatically start and you time to go through the video course and slides till are confident. You will have to send and email asking them to start your lab access to their support. They typically state it to be done within 24 hours, but is actually started within few hours
- When the lab starts, you will have access to Student VM with limited user rights (as per Assumed Breach Methodology) which can be accessed via RDP over VPN or via Apache Guacamole based web interface over Internet. Personally, I preferred using the web interface as it was easier to switch between the apps while researching about a topic, taking notes and capturing screenshots
- Ideally, You should go through the Videos and Slides before starting the LAB Access and then complete both exercises Flags (Portal) and Objectives (Lab Manual) in your the lab.
- Choose your favourite note taking app to document all the objective and flags you have solved with detailed steps and screenshot. I had used OneNote for my note taking (sample screenshot as below).
- Start preparing your cheat sheet of command for each scenario that you have used during the LAB. You may include any additional command or tools encountered outside of the course as well. This is very important as it will save you hours of frustration during LAB & Exam when you are trying to replicate same attack that you have previously tried.
- Cheat Sheet: Red-Teaming/CRTP - Notes & Cheat Sheet (github.com)
- Don't be limited to the concepts taught only in the course, explore the topic on the different blogs and forum like ADSecurity.org, SektorOps, HarmJ0y blog, iRedTeam etc
- It is recommended to do your objectives at least twice, one as stated the Lab Manual and another as a mock exam to prepare your strategy that if you were given fresh vanilla environment how would you approach and plan your attack. This will help you a lot in the exam.
- Lastly, I would recommend to attempt the exam while your lab access is still valid. I had attempted my exam on 14th Day of purchasing the course and I am planning to use the remaining Lab for practicing the same attack using Covenant C2.
3) The Exam
- You get 1 exam attempt included with your Course and It can be started any time you want from the student portal.
- Please note that once you start the exam there is no turning back, you cannot pause the exam and after 24 hours + 1 hours (25 Hours) it will terminate automatically. Therefore it is recommended that you are well rested, fed and hydrated before you start the exam.
- Similar to your Lab environment, you get access to Student VM as Normal Privileged User and you are expected to gain Remote Code Execution Access on each of the 5 machines. There is no flag to capture so you take screenshot after running "whoami && hostname" command as POC.
- Remember to take screenshots of each step that you perform during the exam and save it in you favourite note-taking app with relevant comments. It will help you a lot during the Reporting.
- Perform a thorough enumeration, and before you start exploitation. You should be able to visualize the attack path leading to DA from Normal User. This will give you peace of mind and will enable you to complete the exam it like a Ninja.
Points to Note:
- You will not be provided with any tools in the exam VM, so prepare your Tool Kit in advance
- As stated earlier, prepare your cheat sheet of tools and commands you are planning to use
- Set up BloodHound on your Base machine and ONLY COPY SAME VERSION of Sharphound to exam VM to generate the dump file. Mismatch in the bloodhound and Sharphound version can yield incorrect results
- Exam guidelines clearly states that it does not require you to perform any kind of Brute Force or Cracking the Hash/Tickets, so save yourself from chasing into the rabbit hole.
- You will have ample amount of time to complete the Exam so Do not Panic, if you are stuck somewhere. Take a break, Rethink and then start again
My Experience:
- I had started my exam at 1 PM local time, as I wanted to save the day light the next day. My objective was to complete the exam on first day and use the 2nd day to prepare the report, all within 24 Hours including the Sleep duration.
- I was able to compromise 2 machines within 3 hours of starting the exam, but I got stuck in third machines for a very long time...and the reason was very silly. I knew what needs to be done..but I was using the command incorrectly and it me long to realise it. The reason was that it not covered in my cheat sheet...and the online blog I was referring also didn't mention how to use it correctly...Huhh!.
- After spending 5-6 hours (includes taking break) I attempted again and voila...It was a breeze to finish the remaining 2 boxes in less than 2 hours and gain Enterprise Admin access.
- I was able to complete the exam in less than 10 hours in total, but I think If I hadn't struggled with the third box due to incorrect command and would have chased a rabbit hole...It could have been done in less than 4-5 hours.
- The exam is between easy-medium complexity, but if you miss something in the recon...it may experience hard time. Also, remember there some slight enumeration topic which is not covered by default in course, and requires you to do some additional research.
- You are supposed to submit the detailed report of all the attack path covers on all the machines during the exam. There is no specific template for reporting, however I had customised reporting template shared by TCM Security on below link.
- I had crafted detailed report with all Executing Summary, Scope, and Findings having Description, Risk & Impact, Affected System, Tools Used, Steps to Reproduce, Recommendations and Reference.
- It took me approx. 7 hours to complete my through report spanning across 33 Pages. Now, I am awaiting for my Certificate to arrive in my mail
Notable Mention
The Pentester Academy Support is really awesome, You can not only ask typical support related question but also the technical queries you are facing while solving you Flag or Objectives. The response it usually in less that 30 minutes (slightly depending upon your time zone).
Finally, Big Thanks to Pentester Academy & Couse Creator Nikhil Mittal for this wonderful experience
Course Link: https://www.pentesteracademy.com/activedirectorylab